Digital Privacy 101

Hey all! Thanks for the nice emails about my essay last week. I'm hoping to catch up on email replies once I get all the 2025 tax paperwork done for Montague Commoners, but in the meantime I hope a blanket "thank you" here in the newsletter will make it to most of the people I owe replies to 🤣
Tuesday's presentation on digital privacy went pretty well, so I figured I'd do my best to reproduce it here for those of you who couldn't make it to the library.
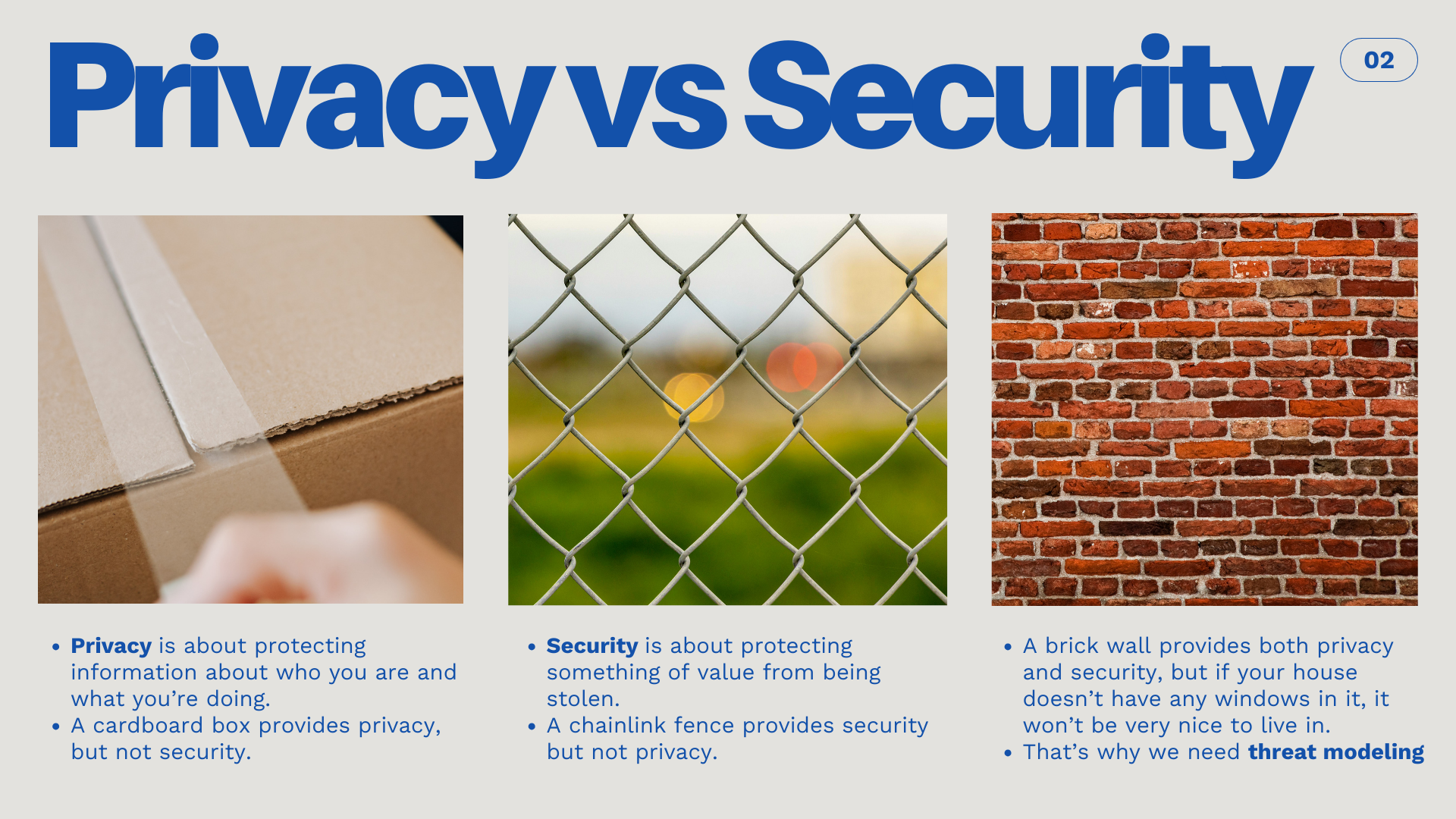
The first step in understanding digital privacy is to understand the difference between privacy and security. Privacy is about keeping your personal information and online activity hidden from people who might want to track you. Security is about protecting information and assets from people who want to steal them. They're closely related fields, and some of the steps I'm going to recommend here will help with security as well as privacy. But it's important to think about them separately to make sure that you're covering all your bases.
(Another important difference is that I am not remotely qualified to talk about cybersecurity. I've been a privacy nerd for decades, and I do my best to keep all my security patches up to date, but I'm sure any half-experienced pen tester could absolutely wreck my sh*t 🤣.)

The next important concept is threat modeling. Unfortunately, there's no such thing as a one-size-fits-all set of best practices when it comes to digital privacy. Everybody's needs are going to be different. And trying to aim for 100% privacy all the time can leave you feeling isolated and paranoid. So it's important to gain a realistic idea of what information you need to protect and who you need to protect it from.
In the next section, we're going to be going over some of the common online privacy threats, who needs to worry about them, and what you can do about them.

Data breaches are one of the most annoying threats out there, because there's very little we can do to prevent them. Huge companies suck up giant amounts of our data, and then they leave a digital door unlocked for anyone to walk in and swipe it. You can check whether your data has been included in any major breaches using Have I Been Pwned. (For those who aren't fluent in spoken Geek, "pwned" rhymes with "owned".)
Data breaches are one of the main reasons that it's important not to use the same password for multiple sites or services. When hackers are able to steal a list of usernames and passwords from one site, the first thing they do is try those username/password combos on all the major email providers, payment processors, and banks. We're going to go over password managers in more depth later, but they make it a lot easier to generate and store separate randomized passwords for each account.

Doxxing is when someone's personal information, often their phone number, employer, or home address, is circulated online to encourage real-world harassment. It's a tactic that mostly gets used against activists and marginalized people by coordinated groups of online trolls. Doxcare is a zine put together by activists who have experienced doxxing, and it covers how to lower your doxxing risk, as well as how to cope with an ongoing doxxing attack.

Data Brokers are companies that compile information about all of us and then sell it for a fee. It can include everything from your name and home address to information about who your relatives are, where you work, what kind of car you drive, and more.
Data brokers are required to have an opt-out form on their website, but you have to go site by site to do it. I've known people who have made a habit out of opting out of 5-10 data brokers every morning while they're having their coffee, and they usually catch up eventually. But there are always new data brokers popping up, so just like weeding a garden, you'll need to keep periodically opting out.
The other option is to sign up for a service that will submit opt-out requests on your behalf. Examples that the EFF mention in their guide include EasyOptOuts and Optery. It means yet another annual subscription to keep track of, but it can save you a lot of time keeping track of things yourself.

Algorithmic targeting is when tech companies use the data they have on you to manipulate your decision-making and behavior. They can predict when you might be vulnerable to impulse purchasing, and what sorts of products you're most likely to overspend on. They can time dopamine rewards to produce behavioral addictions to their products. They can use dynamic pricing to charge more for products when people are desperate and don't have other options.
Algorithmic targeting is one of the main factors that makes big tech bad tech, and the only way to be entirely free of it is to wean yourself off big tech products. Luckily, there's a lot you can do to reduce its effectiveness in the meantime. Adblockers like uBlock Origin and tracking blockers like Privacy Badger can do a lot to reduce the amount of information big tech can collect.
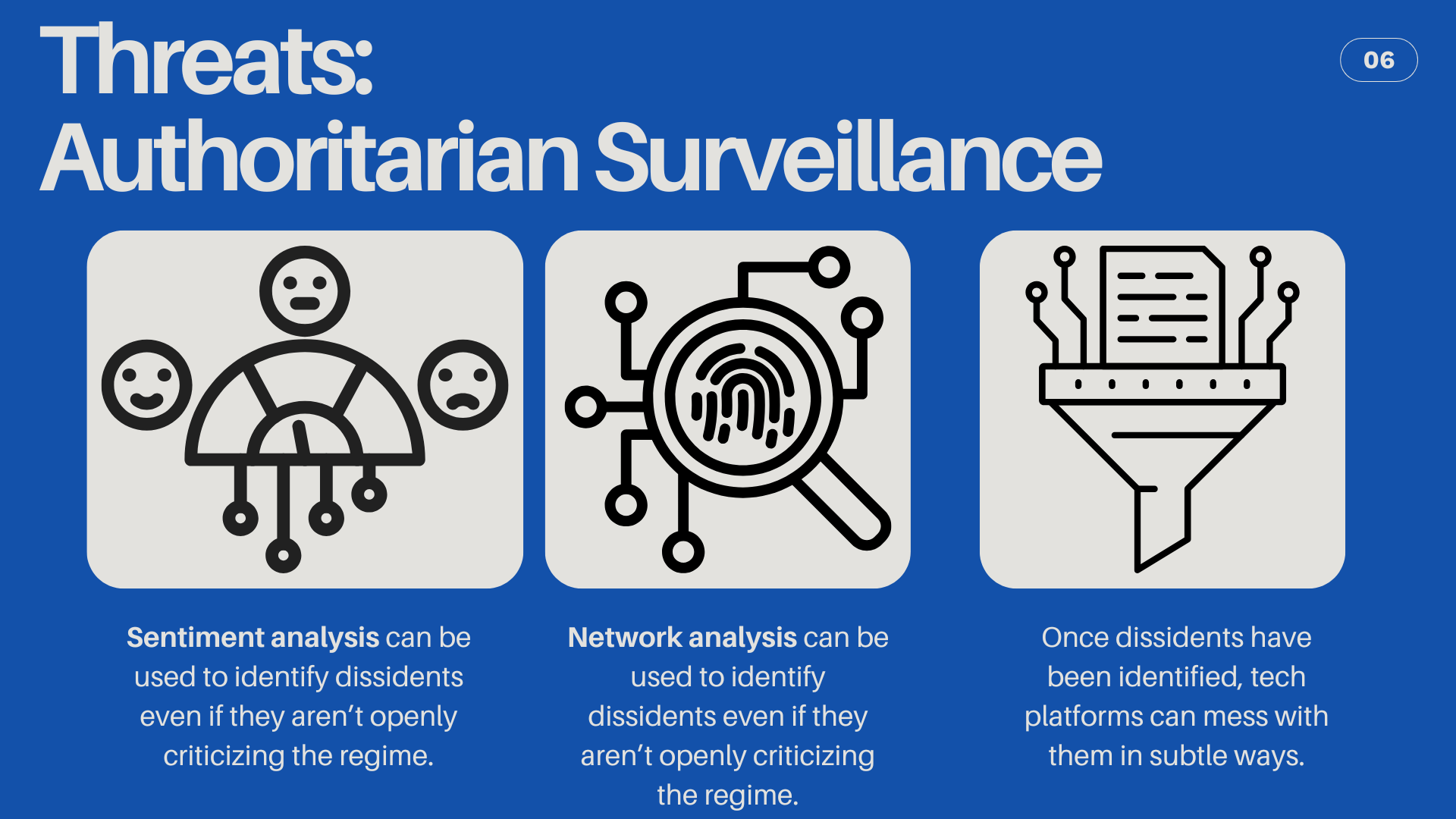
When you're dealing with an authoritarian regime, privacy gets much harder to maintain, and the consequences of disclosure get much higher. The EFF's Surveillance Self Defense guide has a chapter for human rights defenders that includes guides on Signal and WhatsApp, as well as how to develop a security plan and how to circumvent network censorship.
I'm going to leave it there for this week, and we'll go over some of the tools that I mentioned in more detail next week.
Podcast Alert: Movement Memos on Minneapolis

(Link in case the fancy embed thing doesn't work)
Kelly Hayes is one of my favorite organizers to learn from, and I've been listening to her podcast Movement Memos since it started in 2020. In this episode, she talks with some of the organizers at the heart of everything that's been going on in Minneapolis about what they're seeing on the ground, how people from out of state can help the people of Minnesota, and what people should know if they're facing an ICE invasion of their town.
Bandcamp Friday tomorrow!
Bandcamp is a website where indie musical artists can sell their work. They take a much smaller cut that Apple or Google, and they don't waste all the money on Joe Rogan like Spotify. Since 2020, they've been doing a thing called Bandcamp Fridays where they forego their commission entirely so that 100% of what you pay for the music goes directly to the artist. In light of everything that's going on, I wanted to share some of my favorite Minneapolis musical artists, because the Minneapolis hip-hop scene includes some of the most amazing rappers you will hear in your life, and a lot of them are in the streets right now protecting their neighbors.
- Dessa - Tough-as-nails feminism interwoven with everything from Greek philosophy to roller derby. My favorite song: Fire Drills, which explores the dilemmas that come with trying to stay safe as a young woman in the world.
- Guante - A lot of Guante's work carries a theme of hope in dark times. His most recent album, All Dressed Up No Funeral, focuses on the climate crisis and the meaningful choices we can still make to save the future. He was also part of a collaboration project called Sifu Hotman, and their song Matches is one of my all time top 10 favorites.
- Doomtree - A Minneapolis supergroup of performers and producers out of Doomtree records. The combination of flow and storytelling that they're able to bring to a record is immersive in a way that's hard to find.
This Week's Nails!


You made it to the end of the newsletter, and that means you get to see this week's nails! They got a little dinged up before I remembered to photograph them, but I do like the bright pink with the black flakies in it.
Stay safe in all the snow! If I don't see you at the protest tomorrow I'll see you back here next week.

